
We understand that social engineering scams can devastate individuals and organizations. This is because criminals use online communication and psychological manipulation by social engineers to trick users into making security mistakes, exploit human vulnerabilities and gain access to sensitive information or resources. This article will discuss identifying social network engineering scams and provide tips on protecting yourself and your business.
What is Social Engineering Fraud?
Social engineering fraud is a type of scam that involves tricking people into divulging confidential information or performing specific actions that can benefit the fraudsters. Social engineering fraudsters use a variety of tactics, such as phishing emails, phone calls, or even in-person visits, to get information attackers gain the trust of their potential victims.
Once they gain the trust of their victims, social engineering fraudsters will typically ask for personal information such as passwords, banking details, or credit card numbers. They can also request access to sensitive systems or files to obtain personal information or request that victims transfer funds or return money to fraudulent accounts.
How to Identify Social Engineering Scams?
The best way to prevent social engineering attacks and protect yourself from social engineering attack scams is to learn how to recognize them. Here are some signs that may indicate that a social engineering attack scam is targeting you:
- Urgent Requests – Scammers often create a sense of urgency to prompt victims to take action quickly without thinking things through.
- Suspicious URLs – Scammers will often use legitimate links, leading to fake websites designed to steal information.
- Unsolicited Emails – Emails from unknown senders or containing unsolicited attachments can be a sign of a phishing attack.
- Unusual Requests – Requests for personal information, passwords, or access to sensitive systems should always be treated with suspicion.
- Emotional Appeals – Scammers may use emotional appeals, such as claiming that a loved one is in trouble, to trick victims into divulging personal information or transferring money.
How to Protect Yourself from Social Engineering Scams?
Protecting yourself from social engineering scams requires vigilance and good judgment. Here are some tips that can help you stay safe:
Be Suspicious
– Always be skeptical of unsolicited requests for personal or private, revealing sensitive information about financial transactions, or gaining access to sensitive systems.
Verify Requests
– If you receive an urgent request, verify it independently before taking action.
Use Strong Passwords
– Use unique, complex passwords for each account and never share them with anyone.
Keep Software Updated
– Keep your operating system, Software, and security tools up-to-date to protect against known vulnerabilities.
Train Your Staff
– Educate your staff on the various social engineering tactics of media and other social engineering attack tactics and scams and provide regular training to help them recognize and avoid these attacks.
Social engineering scams can be difficult to detect, and their impact can be devastating. However, by staying vigilant and protecting yourself and your business, you can reduce your risk of falling victim to these common scams.
Remember always to be skeptical of unsolicited requests, use strong passwords, keep Software updated, break security practices, and educate your staff on recognizing and avoiding social engineering attacks and scams. These tips can help protect yourself and your business from social engineering attacks and fraud.

Taking a proactive approach to protecting yourself
We recommend taking a proactive approach to protecting yourself and your business from social engineering scams. One effective method is implementing multi-factor authentication (MFA) for all accounts. MFA requires two or more forms of identification to access an account, such as a password and a fingerprint scan, making it more difficult for fraudsters to access user login credentials.
Another useful strategy is to monitor your accounts for suspicious activity regularly. Set up alerts for unusual transactions or changes to your account’s protection settings. By catching potential fraud early, you can minimize the damage caused by social engineering scams.
It’s also important to stay informed about the latest social engineering scams, malicious websites, and tactics. Cybercriminals constantly adapt their methods, so staying up-to-date on the latest threats and security practices is crucial. You can stay informed by subscribing to cybersecurity newsletters or following reputable cybersecurity blogs and news outlets.
In summary, social engineering scams seriously threaten individuals and businesses. By learning to recognize and protect against these scams, implementing security measures such as MFA, monitoring your accounts for suspicious activity, and staying informed about the latest threats, you can reduce your risk of falling victim to a serious social engineering attack, phishing attack, or fraud.
Remember always to be skeptical of unsolicited requests and use strong passwords. With these measures in place, you can help keep legitimate users, yourself, unsuspecting users, and your business safe from social engineering scams.

A common type of social engineering scams
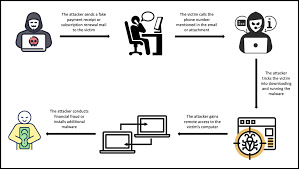
One common social engineering scam is phishing, where scammers use emails, text messages, or phone calls to trick individuals into providing sensitive information or downloading malware. These phishing messages often appear from a legitimate source, such as a bank or a popular website, and may use a sense of urgency or fear tactics to prompt the recipient to act quickly.
To protect yourself from phishing scams, being skeptical of unsolicited messages, especially those that ask for sensitive information or require immediate action, is important. Check the sender’s email address or phone number for signs of suspicious activity, such as background information, a mismatched domain, or an unknown phone number.
Another effective way to protect against phishing scams and malicious sites is to use anti-phishing Software or browser extensions, which can help detect and block suspicious websites’ email links or messages. Many popular web browsers also have built-in phishing protection features that can be enabled to show malicious websites and provide an additional layer of security.
In addition to spear phishing scams, social engineering tactics can also be used in other types of fraud, such as tech support scams, where scammers pose as technical support representatives and trick individuals into paying for unnecessary services or downloading malware. To protect against these scams, seeking technical support from reputable sources and being cautious of any unsolicited support offers is important.
The best defense against social engineering scams is to stay informed, be vigilant, and use common sense. By taking a proactive approach to cybersecurity and implementing security measures such as weak security protocols such as MFA, monitoring your accounts, and using anti-phishing Software, you can help protect yourself and your business from social engineering scams.
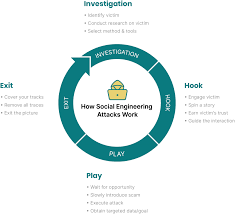
How Social Engineering Scams Work
Social engineering scams use victims’ trust and exploit human emotions, such as fear, curiosity, or greed. For example, a phishing scam may send you an email that appears to be from a legitimate source revealing sensitive information, such as your bank account, asking you to click on a link and enter your login credentials. Once you do so, spear phishing scammers can use your information to steal your money or identity.
Pretexting is another type of social engineering scam that involves creating a false sense of trust with the intended victim first. For example, a scammer might pose as a tech support representative and convince you to install malware on your work or home computer, giving them remote access to sensitive data.
Baiting is another common social engineering scam that involves offering something of value, such as a gift card, in exchange for personal information. Once the scammers have your financial information, they can use it for fraudulent activities.
How to Protect Yourself from Social Engineering Scams
There are several steps you can take to protect yourself from social engineering scams:
Be wary of unsolicited emails, text messages, or phone calls, especially if they ask you to provide personal information or encourage users to click a link.
Check the sender’s email address or phone number to verify it is legitimate.
Install anti-virus software and keep it up to date to prevent malware infections.
Use strong and unique passwords for each of the many users of your online accounts.
Enable two-factor authentication for an extra layer of security.
How to Report Social Engineering Scams
If you think you have fallen victim to a serious social media or engineering scam or received a suspicious email, text message, or phone call, you should report it immediately. Reporting scams can help authorities track down scammers and prevent them from targeting others.
Here are some resources where you can report social engineering scams:
The Federal Trade Commission (FTC) has a website where you can report scams and file a complaint. The FTC also provides tips on how to avoid scams and protect yourself.
The Internet Crime Complaint Center (IC3) is a partnership between the FBI and the National White Collar Crime Center that investigates and tracks Internet scams.
Your local police department may also be able to quickly determine if you have been the victim of a scam.
In conclusion, social engineering scams seriously threaten your financial and personal security. Understanding how these scams work and protecting yourself can minimize your risk of falling victim to them. Remember to stay vigilant and report any suspicious activity to the authorities.

Conclusion
Social engineering scams are becoming increasingly sophisticated, and it’s essential to be aware of them to protect yourself from financial losses or identity theft. Understanding how these scams work and protecting yourself can minimize your risk of falling victim to them.
We hope that this article has been informative and helpful to you. If you have any questions or concerns, please don’t hesitate to contact us. Stay informed and vigilant is the best defense against most social engineering attacks and scams.
CoopBusiness is a revolutionary cooperative business-building platform that empowers individuals to become entrepreneurs, business owners, and financially independent.
As a member, you’ll receive top-level business mentorship, access to our proprietary business systems, and the opportunity to access the funds you want to turn your business ideas into reality.